

Assessment and Remediation
A ransomware attack has been successful in disrupting the client’s IT infrastructure. The customer has already conducted an investigation of the IOC through the use of a third party, and they are currently in the process of implementing tools for permanent remediation. At the time of the project’s inception, the client had the following expectation.
To identify, evaluate, and recommend the best security practices for On-premise infrastructure and Cloud workloads. Also assist with implementing the security gaps, deploy a network resource and initiate the micro-segmentation processes in AWS network, deploy SOC, and manage remotely 24/7.
In addition to that, the customer anticipated that an experienced professional from the sector, particularly in the field of cyber security, would evaluate their on-premises and cloud workloads and submit a report detailing the gaps that were discovered. The customer was approaching Zero Trust adaptation in a strategic manner, and prior to that, they would like to reduce their attack surface on the operations of the organization, to protect vital assets, and restore normalcy while simultaneously improving the defenses of the infrastructure against any future threats. This is the fundamental purpose of the project.
The Approach

We have provided our comprehensive risk assessment questionnaire to IT team to fill-in to understand the client’s IT infrastructure boundary and also to define the project scope, objectives and deliverables. The risk assessment questionnaire can be downloaded from here.
This project will be delivered in 2 phases with four distinct waves.
In phase 1, a security consultant will be deployed who will conduct an evaluation of current security postures, identify potential vulnerabilities, and make recommendations for improvements, as well as assist in the development of a security strategy and its deployment, and who will be available for 8 weeks for this engagement. During wave 3, an Amazon network L3 engineer will be deployed for four weeks to assist us with AWS network Micro-segmentation.
In phase 2, a security L3 will be deployed to set up SOC as directed by the security consultant and to ensure that all network and server components are recorded
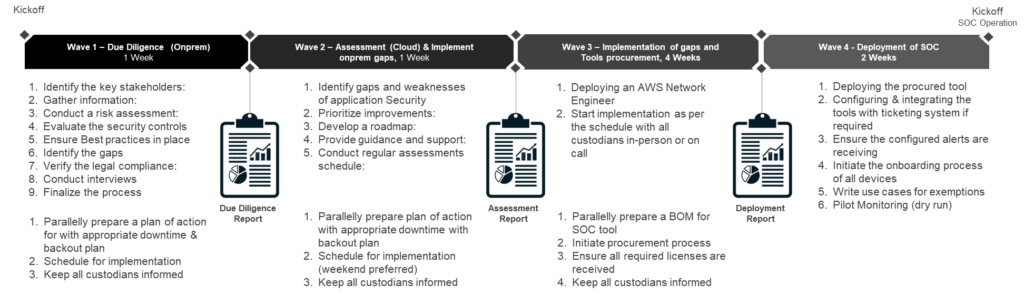
As per the above plan the actions have been performed and delivered it as scheduled.
My Role:
Security Architect, I am accountable and responsible for the delivery of the entire project, from beginning to end. This consists of the assessment & remediation, tools implementation and remediating most critical CVEs.
Project Details:
Team Size: 5 Members Team
Project Duration: 8 Weeks
Project Cost: T&M
The Conclusion:
As mentioned above the actions have been performed and delivered as scheduled, customer also initiated next steps by procuring and deploying a MDR solution, an ZTNA solution with next generation secure web gateway (SWG) for their internet Access, CASB etc.,







