

The last line of defense against Ransomware
Although most businesses have anti-virus software, user guidelines, firewalls, and a secure production platform in place, these measures are typically insufficient to prevent virus infection. To quickly penetrate security and find a safe landing ground to set up control central, ransomware merely needs to find the weakest link, which is usually you and me.
Rubrik is the last line of security in case ransomware manages to infiltrate your network. We don’t stop attacks from happening, but if one does get past your front-line defences, we’ll alert you to it, help you pinpoint the area of impact, and make it possible to restore only the damaged parts with minimal effort. Recovery time is measured in hours, not days.
Our ransomware protection package includes scanning for and eliminating any ransomware that may have infiltrated your system, but it’s just the beginning of our five-part strategy to keep your system virus-free. We take extra precautions to guarantee that the backup platform itself is secure, as well as the data stored therein.
The latest ransomware variants aim to cripple your backup system as a first line of defence. Rubrik’s hardened hardware/software, detection of bad actors, data security, native triple air gap, and security through simplicity all work together to eradicate this risk.
What’s most important is having a system in place to identify and fix damage caused by ransomware.
Exploring and Fixing Ransomware Is Just the Beginning
It’s lunchtime, and you’re planning to get something to eat on the run. You hear a ding from your phone as you head out to your car. The email came from Rubrik, and it seems that they have noticed an abnormality and may have found a ransomware threat.
As you walk back to the workplace, you’re alerted to three more strange occurrences around you. There appears to be a problem. Some of your company’s data and infrastructure have begun to crash. You are currently experiencing the preliminary phases of a ransomware attack.
Rather of waiting for the backup admin to find out about a ransomware assault through frantic phone calls from end users, Rubrik alerts them immediately so they can begin investigating and, if necessary, fixing the problem.
Automatic discovery, alerting/notification, and simple recovery at scale are the three components of this procedure.
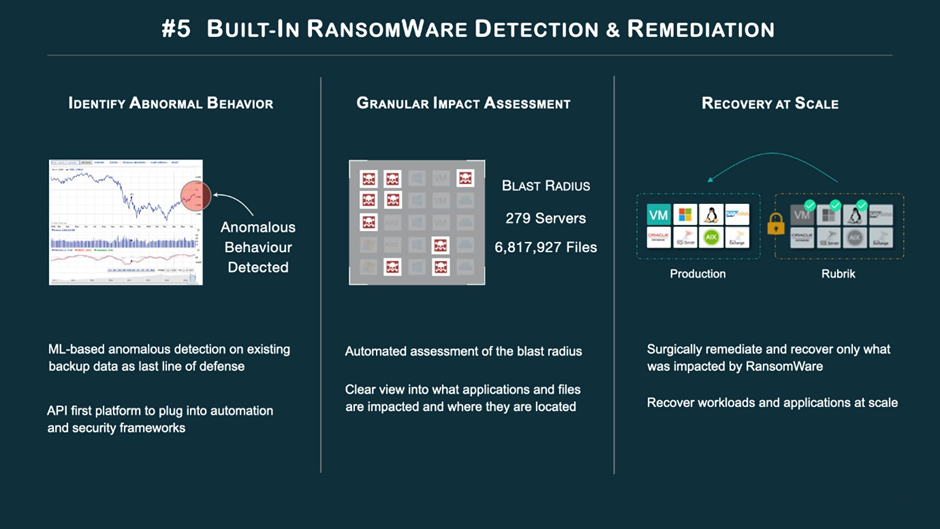
What could be more vital during a ransomware attack than being able to detect the attack early on, quickly pinpoint the affected area, and recover the data with minimal effort? Therefore, it is important to implement automatic detection and identification of abnormal behaviour.
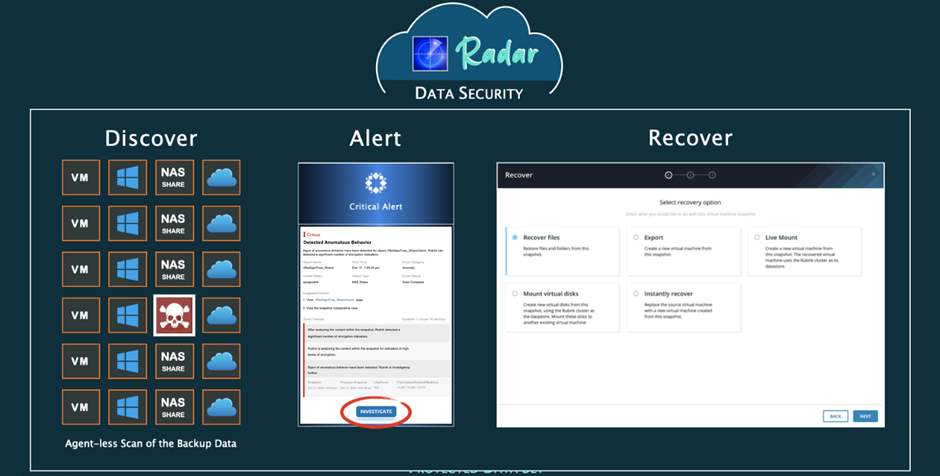
The agentless scans of a finished backup are performed by Rubrik Radar, our built-in machine learning ransomware detection. The backup data’s integrity and the presence of malware-based anomalies are both checked by inspecting the metadata. The Granular Impact Assessment is the next phase in the recovery process once an anomaly has been detected and is accomplished by comparing the most recent backup with earlier backups to determine the precise nature of the changes.
Since it lets you calculate the blast radius of an attack, the Granular Impact Assessment is one of the most crucial, yet often disregarded, aspects of a ransomware strike. If you don’t know what’s been affected by a problem, you can’t hope to solve it. Rubrik streamlines and accelerates what would otherwise take days of manual data exploration to determine what was affected. See the area of assault right away so you may look around and decide if any action is needed.
This brings us to the third and final phase of the ransomware discovery and treatment process: recovering the encrypted data at scale. Once the scope of the attack has been determined, Rubrik makes it possible to recover only the affected files, in bulk. You can do all your investigating, evaluating, and fixing in the same place on Rubrik. No additional equipment is needed.
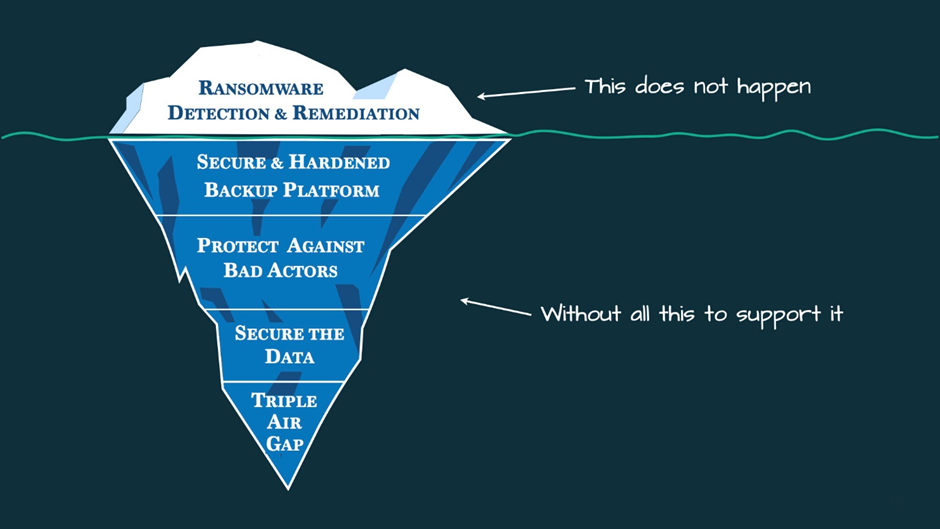
However, the process of identifying and fixing ransomware is only the beginning. Rubrik’s full and comprehensive ransomware security package is like an iceberg with its many levels submerged below the water’s surface. The backup and the infrastructure behind it both need to be safeguarded.
Ransomware and Rubrik’s Secret defense
Though many providers claim to safeguard your data from ransomware, a closer look reveals that at best they just use basic anomaly detections (typically signature-based on not file-based) and leave your backup data and infrastructure wide open. When backups failed to restore their systems, 44% of ransomware-affected businesses paid the demanded sum to get their data back. This is due to the fact that the backups themselves, or the infrastructure used to create them, fell prey to the attack.
A Locked-Down Filesystem with Built-in Ventilation
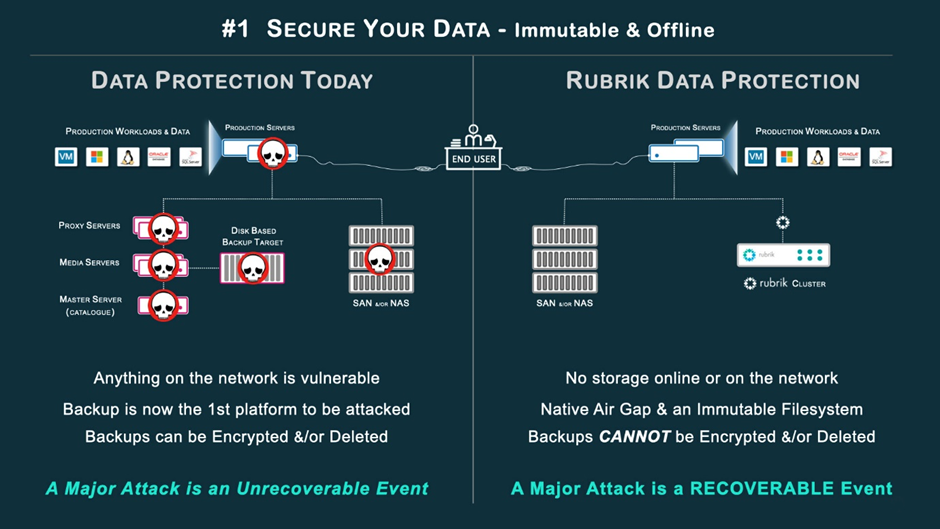
Today, most data protection methods store their local copies on media that can be altered. The information could be compromised, encrypted, or erased in the event of a ransomware attack. Because of this, the ransomware virus has direct access to your backup files, which is a major problem.
By closing the port connections when they are not in use, Rubrik maintains a natural separation between your data and the network. For your data to be recoverable after a big attack, you must store it on an offline, immutable filesystem.
Multiple Spaces for Air to Escape
Triple air gap security architecture deployment is a basic backup approach for ensuring data integrity and availability. Air gapping means isolating anything from its network, the internet, and, if at all feasible, physically removing it from its environment. There can be no damage to the data if the hackers cannot access it. Triple Air Gap architecture is a design choice by Rubrik that blends native air gap elements with physical air gap features. The aim is to guarantee that the native air gap feature will offer a level of protection against ransomware not available in other solutions, even in a single cluster design (Rubrik cluster in the production data centre only).

First Air Gap: During Production, Inside the Data Center
For finer-grained control over the connection process during backup and recovery, the Rubrik platform interfaces directly with the applications, hosts, and hypervisor in your environment. Backups are started by Rubrik, which also opens the necessary ports, encrypts the data, and pulls it onto the Rubrik immutable storage platform for safekeeping. After a successful backup, the port connection is closed and stays that way even when not in use. A natural separation is thus preserved between your production data and the Rubrik cluster.
Since backups are always started on the Rubrik cluster and can be recovered rapidly in the event of a significant attack, this architecture is preferred when protecting sensitive information. These components are important to our comprehensive strategy to defend backups from ransomware.
Second Ventilation Interval: Inside the Emergency Relocation Site
Use secure replication to set up a second Rubrik cluster in the DR data centre, effectively creating a dual air gap architecture. In addition to replicating data from the primary DR cluster, the secondary DR Rubrik cluster uses offline storage, closes ports when they are not in use, and uses pull replication. The disaster recovery cluster is responsible for starting replication, opening ports, and retrieving encrypted copies. After replication is finished, the ports are closed and left that way while the machine is not in use. Between the two data centres, a Firewall can be set up for further security.
Data is quickly recoverable from either data centre after a catastrophic attack because to this architecture’s dual cluster air gap design, which ensures that backup data and storage are not accessible in either data centre by keeping ports locked when they are not in use.
Space in the Atmosphere 3: The Underground Storage Room
Automatic archiving to any destination, including the cloud, disc, or tape vault, is now possible with Rubrik. A third, completely separate copy of your crucial backup data is made in this way. This archival copy, along with the other two air gap clusters, is currently down and unavailable. If no archiving or restoring is currently taking place, the connection will remain closed.
All archival activity can be started and dispatched from either of the two available Rubrik clusters (air gap #1 or air gap #2), and there is no need for a catalogue to be kept on hand because archives are self-describing. All you need is the decryption keys, and you can restore archives to any Rubrik cluster. Catalogs are frequently attacked by ransomware because they can be used to make backups and archives useless. Rubrik doesn’t have a catalogue that could be compromised.
Your backup data is protected from ransomware if it is kept on an immutable platform that is offline and inaccessible, in addition to a triple air gap architecture. How about the data storage system itself? Windows-based devices, including proxy servers, management servers, media agents, and catalogue servers, are susceptible to ransomware. The Rubrik backup platform is protected from ransomware in the following ways. To begin, we make sure the underlying hardware and software are safe and hardened.
A Robust Data Backup System
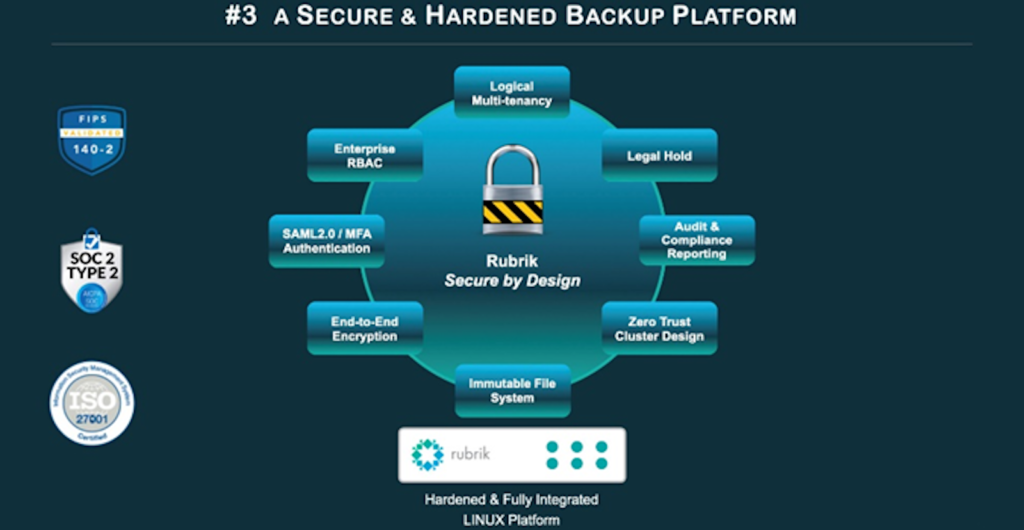
A Secure and Completely Integrated Linux Filesystem
To begin, we employ a secure and feature-rich Linux filesystem. Windows and other non-hardened filesystems are widely used by backup solutions, making them susceptible to attack and encryption. If the system you use to restore the data is likewise infected with Ransomware, the backups are useless. We guarantee that this will never happen on Rubrik due to our secure Linux filesystem.
Uniform Data Format
In our system, information cannot be changed or removed once it has been entered. A hundred percent of data stored in Rubrik cannot be changed… Given how important this is to the security of your information, it bears reiterating. Your data on Rubrik is completely immutable and safe from ransomware.
End-to-End Data encryption
All data stored in the Rubrik fabric is encrypted at rest and in transit. The use of AES-256 software encryption ensures the safety of data whether it is being transferred between devices, sitting idle on a hard drive, or saved in the cloud. Files stored on hard drives can be encrypted for added security.
SAML 2.0/ MFA Authentication
With the help of Security Assertion Markup Language (SAML), an open standard is established between user authentication and service access permissions. When MFA is also used, the backups are safe from hackers and other intruders who may have gained access through compromised accounts.
Data access credentials and permissions are targeted by ransomware. While Windows Active Directory is a prime target for ransomware, once compromised, hackers have complete access to all backups just by signing in through the main door. Even if a hacker steals administrative privileges from Active Directory (AD), SAML/MFA mitigates this risk by requiring them to prove their identity using a token or another form of multi-factor authentication.
Enterprise RBAC
With Role Based Access Control, you may restrict user access to specific data and operations within your Rubrik cluster. In addition to Active Directory users and groups, RBAC can also be set up for local users and groups. This additional layer of protection guarantees that users never breach the backup administrator-set security standards.
Logical Multi-tenancy
Multi-tenancy groups allow for the logical grouping of users, items, and permissions. This offers granular administration of user activities with the ability to report and monitor group and individual actions inside a group….and sure I used the term group 5 times, actually 6 now, in this two-sentence paragraph.
Legal Hold
A “legal hold” stops data from being erased or altered before a certain date and time has passed. Backup administrators have the option of putting any Rubrik item on legal hold and defining what that means in the event of an audit or legal action. These safeguards can only be dismantled when both parties provide the official go-ahead for the Rubrik Security Support team to do so.
Records of Auditing and Compliance
Automated and timed reports with a high level of detail. These in-depth reports make it simple to keep tabs on audit and compliance to check if all security policies are being followed within an organisation. These emails can be automatically emailed to key stakeholders.
Zero Trust Cluster Design
In a zero-trust security model, granting permissions is explicitly forbidden.
Safeguarding Against Malicious Entities
While there are many measures that may be taken to keep outsiders from accessing an organization’s data, protecting against malicious insiders who could try to compromise backups or prevent data recovery is another matter together.
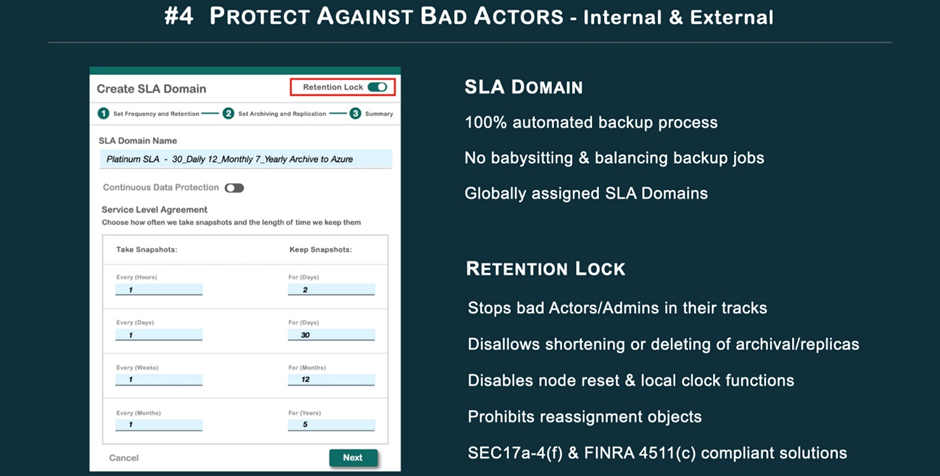
To keep malicious actors from tampering with backups or data, Rubrik employs two essential technologies: the SLA Domain and the Retention Lock.
Backup Automation in the Service Level Agreement (SLA) Domain
When it comes to BACKUP, the SLA Domain automates the whole process. Not having to micromanage backups, schedules, and problems is a big deal. It gets rid of the need for backup procedures altogether.
Lock-In Effect
Because of this, once an SLA Domain has been assigned to an object or objects, it cannot be removed or reassigned. This means that the backup schedule, retention period, and storage location cannot be modified under any circumstances. As a result, unscrupulous actors can’t reassign policies to shorten data retention terms.
This prevents archives and replicas from being truncated or removed. You may not think about it, but Retention Lock also prevents hackers from doing things like resetting the cluster using the command line interface (CLI) or tampering with the clock settings to change the date to 2025 and fraudulently expire the long-term archives.
The Man Behind the Curtain Is Rubrik Radar
Our Polaris SaaS platform has a feature called Radar that enables Rubrik’s Ransomware killer. Radar’s sole purpose is to ensure that your backups are always virus-free. Radar performs agentless scans of your backups, flags aberrant malware behaviour, determines the blast radius, and enables simple repair of your affected data with zero infrastructure and in minutes.
However, since ransomware has become so popular and lucrative, hackers keep developing improved variants. The next generation of ransomware will be more sophisticated, stealthy, and disruptive than ever before thanks to Machine Learning, artificial intelligence tools, and hacker collectives. The only way for data protection solutions to stay ahead of cybercriminals is to anticipate their moves and anticipate their needs.
“Skate to where the puck is going to be, not where it has been,” or “Look to the future while being conscious of the present,” were both sayings attributed to Wayne Gretzky. To stay ahead of the next generations of ransomware/malware outbreaks, Radar employs the same Machine Learning and AI capabilities that cybercriminals utilise. Radar has one primary goal, and that is to ensure that your backup data is safe from viruses. We accomplish this by keeping our attention on today’s ransomware viruses and preparing for tomorrow’s ransomware with the resources available then.
Final Thoughts on Neutralizing Ransomware
As a result, ransomware is now a common occurrence. Despite organisations spending billions to safeguard their production data, the global incidence of cyberattacks is on the rise. This highlights the fact that the weakest link is not technology but rather people, which is why ransomware is so effective.
If this is the case, then the statement “It becomes more WHEN versus IF in relation to facing a ransomware attack” is correct.
If what was just said is true, then data recovery from backups should be a top priority. While spending on up-front protection is still essential, being able to bounce back quickly after a ransomware assault has become equally crucial.
To ensure you can use backups to recover from ransomware, your backup platform should be able to survive attacks themselves and always be ready to restore data in the case of an attack.
Ransomware-killing Rubrik. It disables ransomware.
It helps enterprises detect ransomware attacks, determine the blast radius, and recover corrupted files. No ransom, protracted outage, company reputation damage, or lawsuits… Maybe peace of mind from knowing your data is safe against ransomware is most important.







