Ransomware is defeatable
Ransomware can be defeated; however, we must have a comprehensive strategy.
The two most significant security risks we face today are Cy-X attacks (Ransomware) and double extortion (Data Exfiltration + Encryption). Every month, hundreds of companies of all sizes fall prey, even with the most advanced technical safeguards in place, and we haven’t figured out how to stop it. Although preventing these attacks can feel like a challenging battle, there is a model that can help, We will do a deep dive onto this today to find out a holistic strategy
Before delving further, let’s examine the techniques used by cyber-attackers.
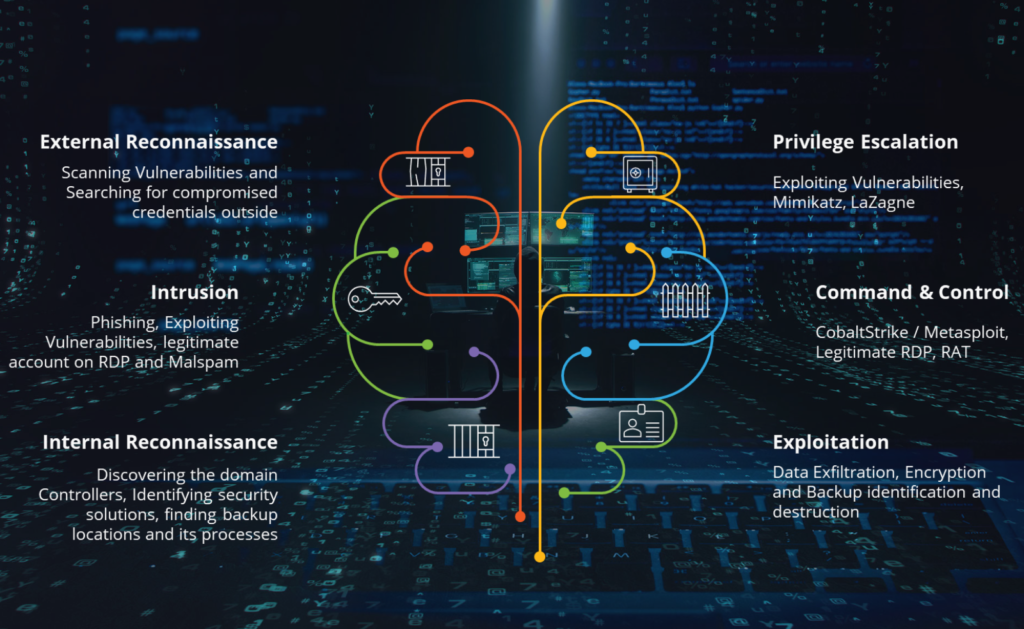
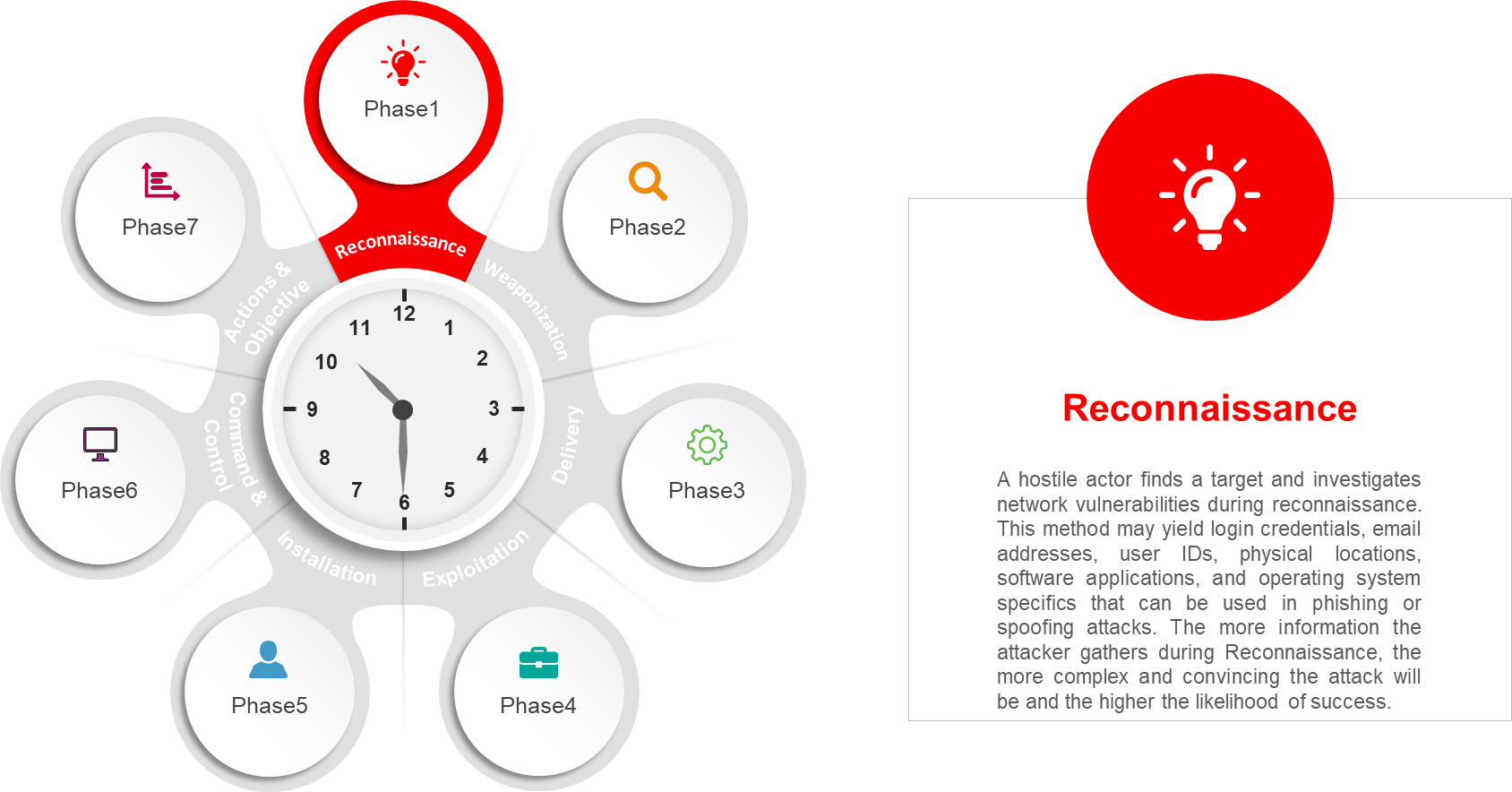
External Reconnaissance: External reconnaissance, also known as external information gathering or OSINT (Open Source Intelligence) gathering, is the process of collecting publicly available information about a target from various sources outside the target’s network or organization. This type of reconnaissance is often a preliminary step for malicious actors to understand the target’s digital footprint and potential vulnerabilities. Using this technique, the malicious actors seek compromised credentials outside of the victim’s information system while scanning for vulnerabilities.
Intrusion, refers to the unauthorized and unwanted access, entry, or presence of an individual, software, or entity within a computer system, network, application, or device. Intrusions can lead to data breaches, unauthorized access to sensitive information, service disruptions, and various other security incidents.
Internal reconnaissance, also known as internal information gathering, is the process of collecting information about a target organization’s internal network, systems, and infrastructure from within the organization’s own environment. Unlike external reconnaissance, which focuses on gathering information from publicly available sources, internal reconnaissance involves collecting insights and data from within the organization’s internal network to assess security vulnerabilities, identify potential risks, and understand the organization’s internal digital landscape.
Privilege escalation refers to the process of exploiting vulnerabilities or weaknesses in a system or application to gain higher levels of access or privileges than originally authorized. This can be a significant security concern, as unauthorized privilege escalation can allow attackers to access sensitive data, perform malicious actions, or compromise the entire system.
Command & Control refers to the communication infrastructure and techniques that hackers or malicious software use to control compromised systems remotely via
Exploitation refers to the act of taking advantage of someone or something for personal gain, often without consideration for the well-being or rights of the exploited entity. This concept can apply to:
So these are the methods that our cyber-attacker personas utilize in their day-to-day lives; now we will learn how to methodically address this using a model that is considered to be the industry standard and is known as the “Cyber Kill Chain (CKC)” Before we continue, let’s first examine what the Cyber Kill Chain is and how it operates.
Cyber Kill Chain Model
The cyber kill chain is a way to analyze a cyberattack that was developed by Lockheed Martin using a military model as its inspiration. It is a step-by-step method with the objective of recognizing and terminating harmful activity.
Organizations typically rely on the cyber kill chain as their primary line of defense against the most sophisticated forms of cyberattacks. These attacks can take the form of ransomware, security breaches, or advanced persistent threats (APTs).
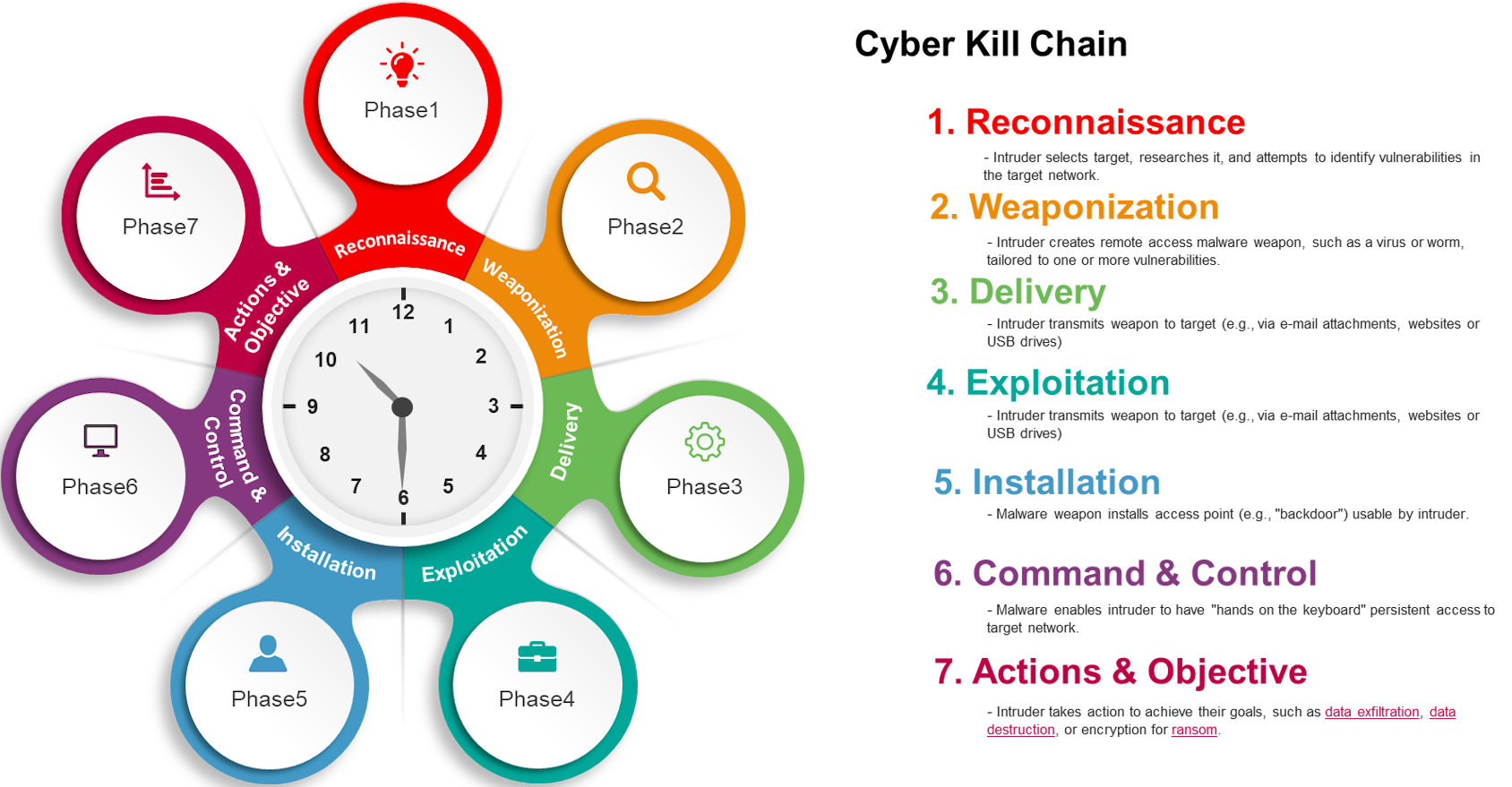
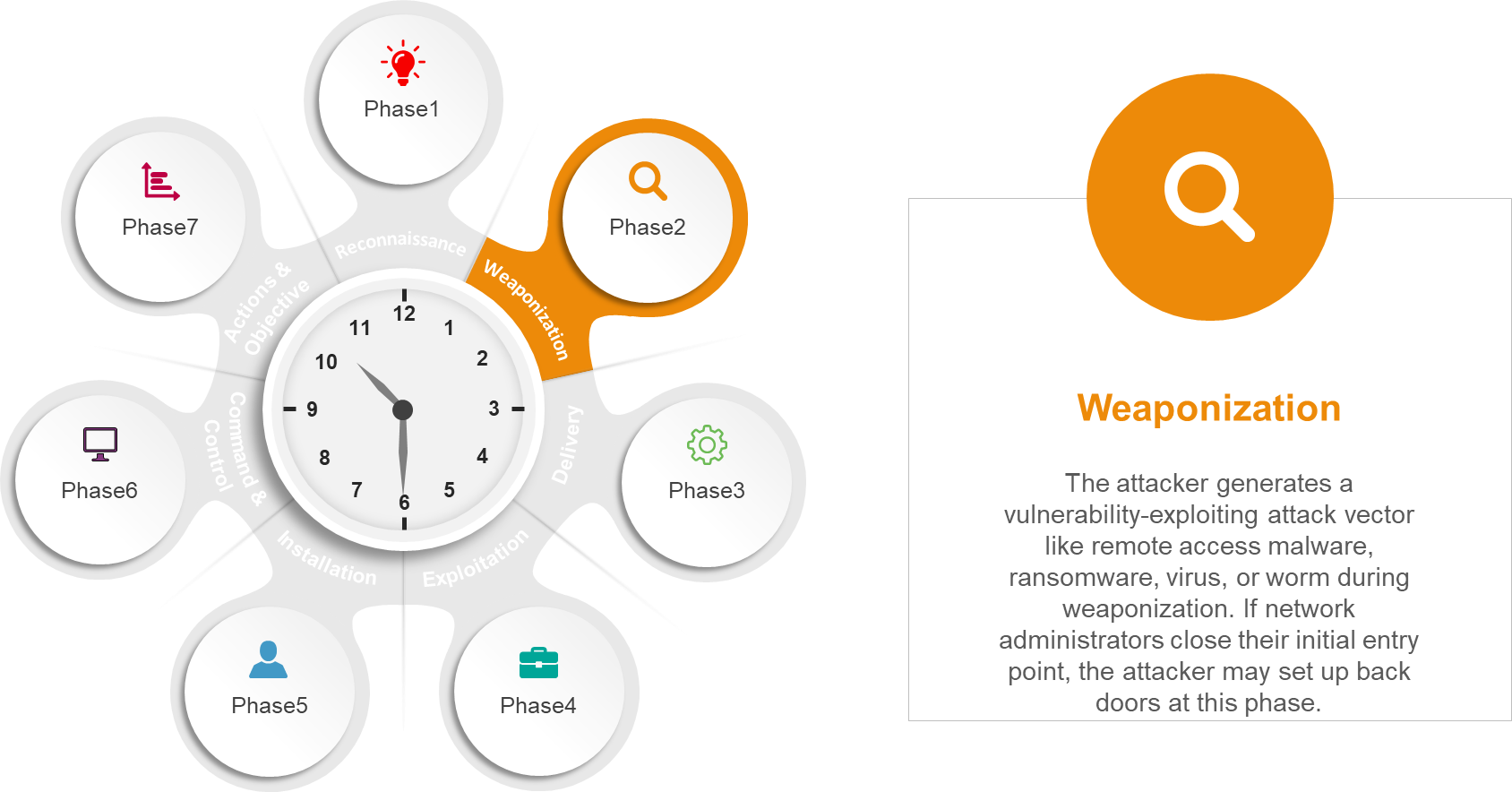
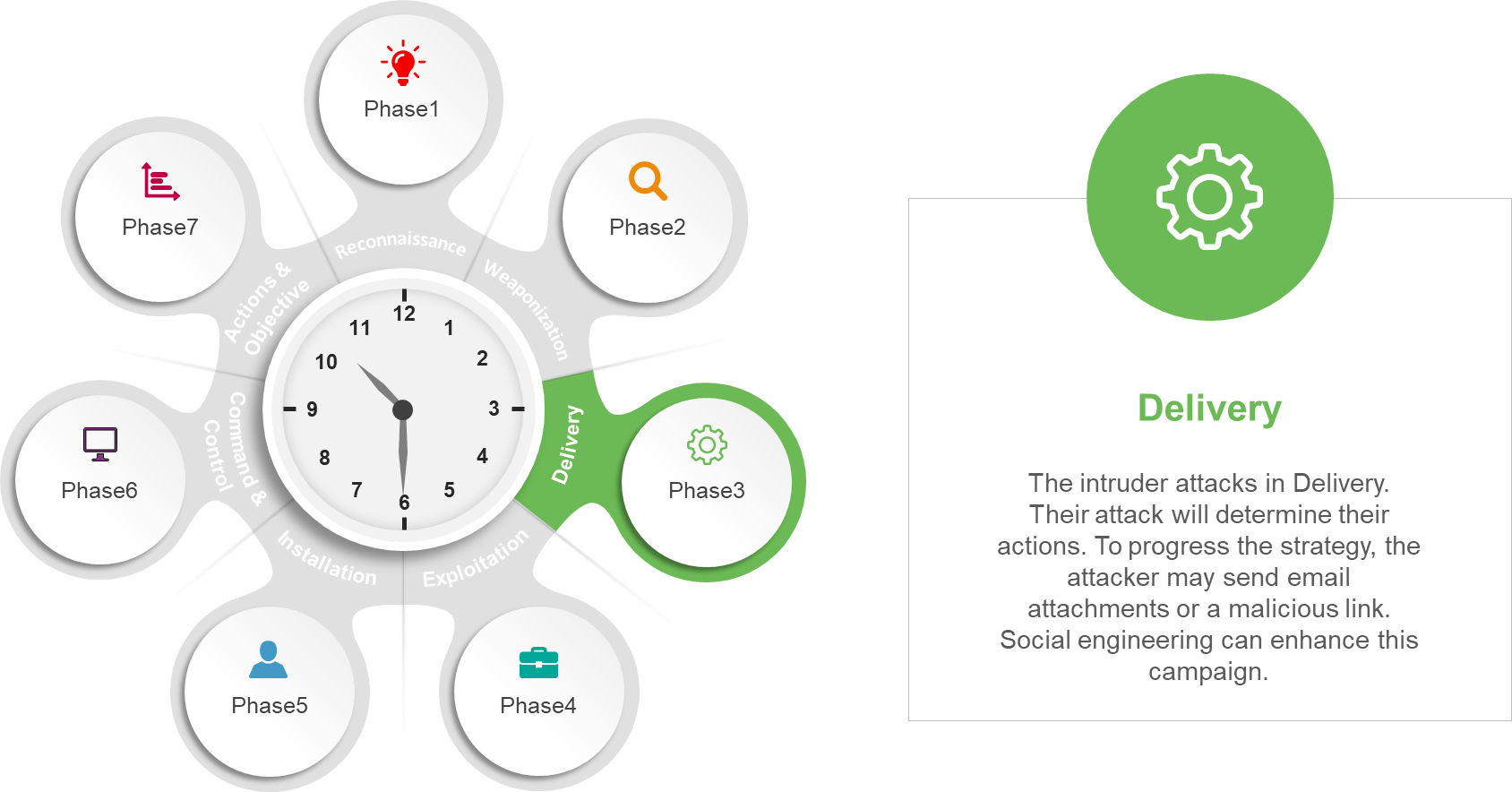
In spite of the fact that the first model of the cyber death chain consisted of only seven stages, cybersecurity experts have since enlarged the concept to include eight stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, actions on objective, and monetization.
How it works?
The “cyber kill chain” is not a security system. Instead, it is a framework that helps security teams predict how attackers will act so they can stop them as quickly as possible or prevent them if the attack has already happened.
The cyber kill chain shows exactly what an attacker will do so that security teams can figure out where most hacks start. Cyber kill chain simulations let security teams get hands-on experience with how to deal with a cyber threat, and evaluating the reactions to simulations can help organizations find and fix any security holes.
It can help with strategy, training, and tool selection by showing which parts of a security strategy, like staff training, endpoint security software, or VPNs, may or may not need to be updated.
Security Controls used to stop Cyber Kill Chain:
The information that is presented below demonstrates, with the assistance of a variety of different security technologies, how each of the security measures can be implemented at each point of the kill chain.
Lockheed Martin provides the following layers of control implementation for the Cyber Kill Chain:
For our purposes, we’ll add one more layer:
Cyber Kill Chain Controls Matrix:
An organization’s controls at each stage of a cyberattack are represented in the Cyber Kill Chain Controls Matrix below, along with how those controls interrupt, stop, or eliminate an attack.
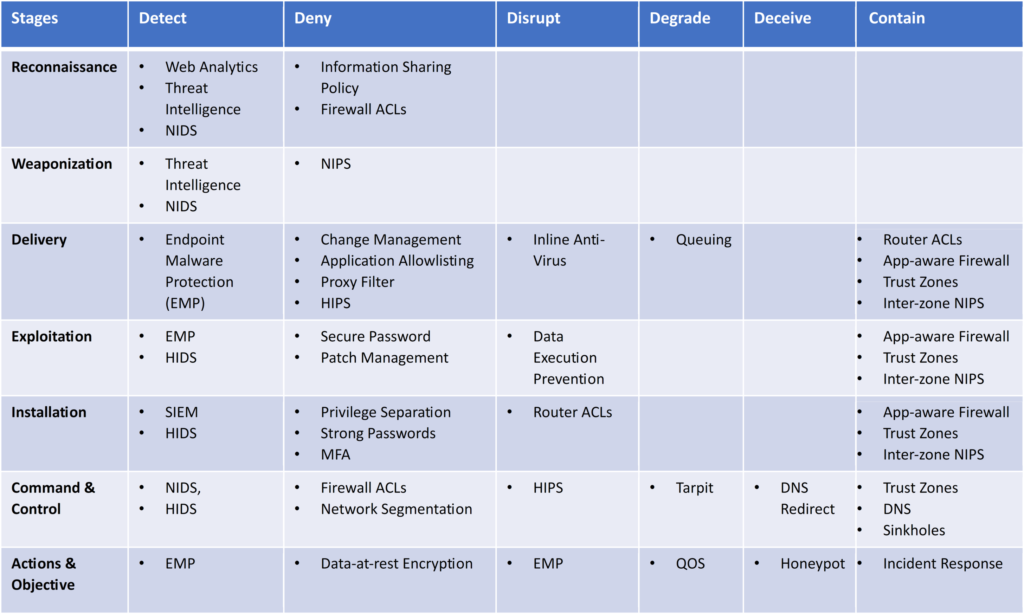
Source: SBS Security
That sums it up nicely; it really is that easy! You should have already included the determined controls in your IT Risk Assessment. If you’re working on a defense in depth strategy, the Cyber Kill Chain can help you see its growth and improve it. By zeroing in on a certain weakness (say, detection) you may strengthen your defenses and determine whether or not an attacker is even trying to breach your system.
In less developed companies that lack the ability to fool an attacker, for instance, some regions will have more restrictions than others. It’s fine if you don’t know how to configure a honeypot or a DNS Redirect. But knowing about those extra safeguards just hire a security consultant like me or talking to your Managed Service Provider (if any) and asking how do they can assist you evolve in these areas?
Note: There is another framework available that was derived from NIST; I will discuss it when time permits (or I’ll write another article on it and provide a link here).
Conclusion:
Cyberextortion is an epidemic. The damage is increasing exponentially. An incident can have a significant impact on the “direct” victim, as well as secondary and tertiary victims whose private information may have been compromised or who rely on the original victim for products or services. Every industry is prey for the competent and determined competitor. Security professionals and CISOs should prioritize ransomware defense.