

Best Practices for Cloud Security
This cloud security article outlines the problems that companies face today, as well as best practises for securing and managing cloud-native products and tools, as well as comparisons of cloud-native security products
Cloud techniques have been implemented to varying degrees by organizations of all sizes. While the cloud is useful in many ways, it also presents hazards that enterprises should fully examine before putting assets there. We set out the problems of securing the cloud environment, as well as how to build best practices for managing cloud security, in this thorough article, complete with links to more information.
Significance of cloud security:
Business-critical applications and data are migrating to trustworthy third-party cloud service providers (CSPs) as enterprise cloud usage expands. Most major CSPs provide standard cybersecurity tools with monitoring and alerting functions as part of their service offerings; however, in-house information technology (IT) security staff may find that these tools do not provide adequate coverage, implying that there are cybersecurity gaps between what the CSP provides and what the enterprise requires. This raises the possibility of data theft and loss.
Business executives must assess the benefits of cloud services against the data security risk they are ready to take because no organization or CSP can eliminate all security risks and vulnerabilities.
Preventing data breaches, noncompliance, and company disruption requires proper cloud security practices and policies (BC). The cloud’s main benefit is centralizing and securing apps and data. Eliminating hardware reduces corporate costs and management while improving dependability, scalability, and flexibility.
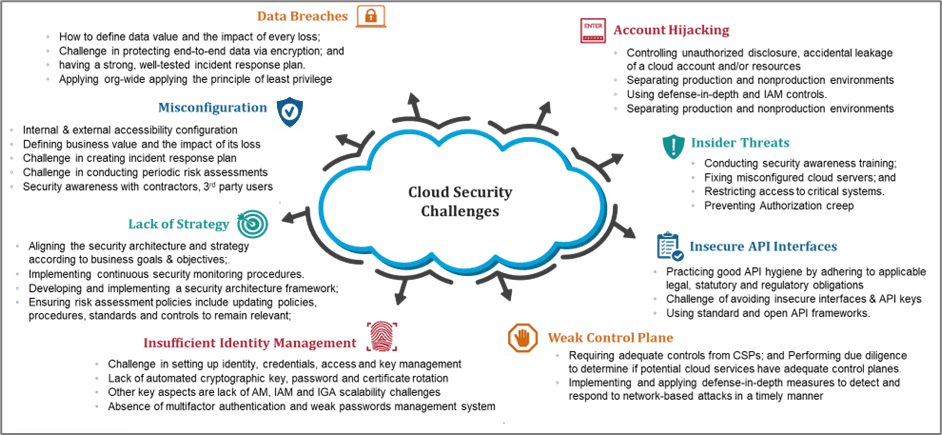
The Cloud Security Alliance listed the most prevalent cloud security concerns to show enterprises the large attack surface that cloud computing brings. The alliance’s biggest issues included data breaches, a lack of visibility, and the following:
misconfigurations and inadequate change controls; absence of cloud security architecture and strategy; poor identity, credential, access, and key management; account hijacking; insecure interfaces and APIs; and abuse and criminal use of cloud services.
Cloud attacks explosion radius grows exponentially. “An attack on a single user’s credentials stretches well beyond the targeted victim, often affecting the entire firm and its clients as well.”
Because private, public, and hybrid cloud environments offer perks and cons, organizations must carefully choose one. A public cloud strategy might relieve an organization’s IT team of system management. However, a public cloud provider may not be as security conscious as the enterprise, leaving security holes.
An organization may have more security in a private cloud, but cloud expenses may climb. A mixed public-private model may appear ideal, but regulatory enforcement across settings is difficult.
How does cloud security work?
Cloud computing exists in three distinct environments:
- CSPs provide hosting for public cloud services. Software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS) are examples of these
- Private clouds are managed or hosted by a single organization.
- Hybrid clouds combine public and private clouds.
As a result, there are two types of cloud security mechanisms: those provided by CSPs and those deployed by consumers. It is crucial to note that security is rarely entirely the CSP’s or the customer’s responsibility. It is usually a collaborative endeavour with a shared responsibility paradigm.

Cloud security best practices:
Organizations trying to adopt the latest innovation and digital transformation have concerns about cloud data security. Cloud computing companies prioritise data integrity and business continuity. Security is crucial for company procedures and customer data. Let’ see how to secure cloud data.
After choosing the cloud for data, apps, platforms, and infrastructure, a business must build a cloud security policy. The policy should address key issues like employee cloud use, data kinds, access limits, and more.
Our cloud security policy template to guide enterprises through policy formation. Other methods include altering an existing infosec policy or employing tools.
Best practice #1: Choosing a right Provider
If you have already done this step, please feel free to skip this step.
Trusted service providers are best for cloud security. We want a cloud provider with the greatest security protocols. We should hire a reputable cloud computing service provider. Examine the service level agreement and other publicly available data before choosing a cloud vendor. These factors ensure service reliability and experience with our organization’s needs.
Trusted vendors have security certifications and compliance. Reputable vendors such as AWS, Azure, Google Cloud, and Alibaba Cloud all offer seamless access to their compliance and security certifications.
Best practice #2: Authentication, Authorization
Let’s start with how users access resources. Cloud providers handle authentication differently, making it confusing. Some providers allow clients to integrate their identity providers, such as Active Directory (AD), via SAML, Open Authorization, or OpenID Connect. Almost all providers offer MFA nowadays.
Security teams must know what services are used and what options they support to navigate this. This context helps admins choose the right authentication technique. SSO coupled to AD can be clever if external application providers support it. This ensures application password and account policies match.
Best practice #3: Attention to Data Encryption
Cloud computing providers should consider this. Data interception is a major threat to data confidentiality. It is recommended to use strong encryption for data in transit and at rest. Before uploading to the cloud, use our own encryption, Cloud providers may encrypt the data. However, they can obtain our encryption keys.
TLS the best which protects data in transit on most communication paths. Some providers automatically activate this, while others need customers to enable it. Teams must research security methods to identify which applicable to services. If possible, enable data encryption too.
Best practice #4: Inventory
This is predominantly required for Software as a service model. Every SaaS security checklist should include finding untracked SaaS usage. SaaS’s quick application deployment is appealing. Beware of unexpected usage. Use manual and automated data collection methods to track consumption and establish a reliable inventory of the organization’s services and users.
Best practice #5: Consider CASB
If a CSP or SaaS supplier can’t provide enough security, consider CASB tools. A CASB lets enterprises apply SaaS-provider-unique controls. These tools can help overcome cloud provider security shortcomings. CASB Provides 4 key features

Hence, use of CASBs become essential for cloud security as it increases cloud security between us and our cloud provider.
Best practice #6: Access Control Policy
Policy-based user access control is another good cloud security approach. It lets us manage cloud service users. Bad-faith employees should know the dangers and consequences of violating business security. Our organisation must restrict cloud service access. Use individual user authentication to control access.
Best practice #7: Educate Users
As a key best practice, train all production or business users, system users and other stakeholders in secure cloud computing. Let’s educate all our resources about Nefarious activities, viruses, phishing emails, malware, and other risky behavior(s).
Our company’s professionals must learn about the risks of strange emails, unrecognised users, and malware-containing files. Employees should be trained to detect and prevent these hazards.
Hence for cloud security, following the industry’s best practises are always good. Consumers like us should investigate data security and service level agreements predominantly before choosing a cloud vendor.







