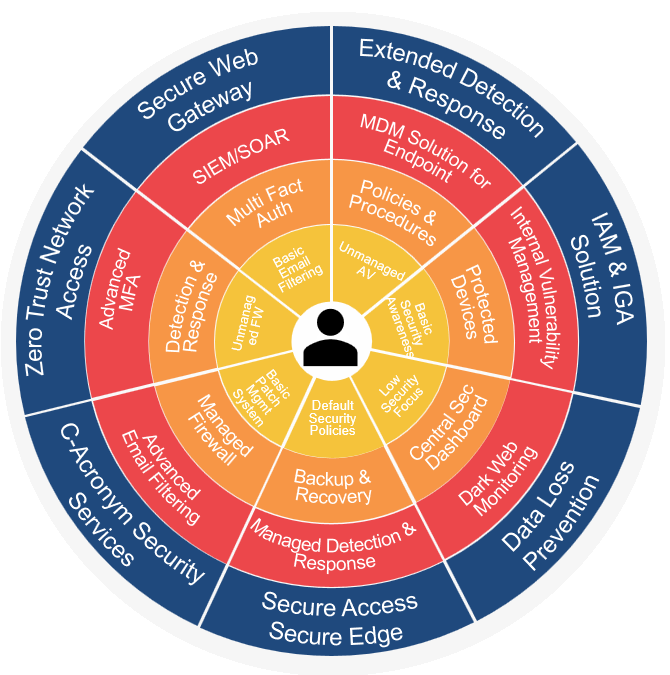
Levels of Security
There is no universal need that every company must achieve Security Level 4 plus a CISO. The suggested Security Level for your organization is determined by the specific risk considerations associated with your company, the size of your IT footprint, and the sector in which you operate. Read through the explanation of each Security Level to have a better grasp on the appropriate level for your company.
Level1: Basic
At this level, organizations have only a few fundamental unmanaged security capabilities at their disposal. Because there is currently no one actively monitoring these tools, there is a good chance that their maintenance will be subpar. It is not advised that any firm operate at this level; however, a home-based or hobby business with a low number of risk factors and a modest IT footprint could operate at this level.
Level2: Standadized
The recommended minimum level of security for any and all businesses. Even if you only implement Multi-Factor Authentication (MFA), Recovery Readiness planning, and MDR, you will be protected against a sizeable proportion of threats. If the components of security described in this level are not already in place in your business, addressing this deficiency should be your top priority.
Level3: Rationalized
Attaining this degree of cybersecurity should be a goal for any company that understands the importance of the topic. The level of security that your firm possesses has dramatically increased at this point. The combination of SOC and SIEM will provide your company with a specialist security team that is always on the lookout for potential dangers in the environment in which it operates. When you reach this stage, you are no longer simply reacting; rather, you are controlling your weaknesses in a proactive manner.
Level4: Dynamic
Companies that operate in highly regulated sectors or deal with information of exceptional value ought to operate at this level. To get to this level will require a significant commitment of resources as well as the cultivation of a culture with a focus on security. To ensure that your team adheres to the stringent standards and procedures that are associated with this degree of security, you will need to implement a security culture that is driven from the top down.
Conclusion:
The executive within a business who is in charge of information security is referred to as the Chief Information Security Officer, or CISO for short. The key accountability of CISO is to conduct periodic assessments of the environment by auditing with a third party and align the security landscape accordingly