

How do we choose which EDR tool to use?
Endpoint attacks are getting more common and smarter, and the number of people working remotely has gone up recently. This makes it clear that companies need strong Endpoint Detection and Response (EDR) solutions. But with so many EDR tools on the market, it can be hard to choose the right ones for your business.
My articles have helped various companies choose and use EDR tools for a long time and with great success, and I’m happy to share what I’ve learned. In this article, I’ll share some tips and factors that I’ve used to help our clients find EDR tools that fit their needs well.
What is EDR?
EDR stands for endpoint detection and response, and Gartner defines it as “solutions that record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected systems.” EDR systems are required to deliver these four core capabilities, among others:
What Criteria Should We Consider to choose a right tool?
My years of experience working with customers have allowed me to design the following criteria that, when applied to the process of selecting EDR technologies, have proven to be quite beneficial.
To be compatible with all the operating systems used in the organization.
Take into consideration the possibility that endpoint devices will be necessary in order for EDR tool agents to run. In order to accomplish this, the agents need to be able to function on each of the operating systems that are used by your endpoint devices.
Containment & Remediation Capability
To stop malware or intruders from accessing your priceless corporate assets, some of the more strong EDR technologies have the capacity to isolate and contain possibly compromised endpoints from the rest of your network. Damage to your surroundings can be significantly reduced or even prevented with containment and isolation.
Next-Generation Anomaly Detection
As the sophistication of endpoint attacks increases and the number and diversity of endpoint devices multiplies exponentially, EDR tools must become more intelligent in order to detect anomalies in endpoint activity that may indicate cyberattacks. It is crucial to discover EDR tools that utilize Next-Gen technologies such as machine learning, artificial intelligence, and behavioral analysis to quickly sift through massive amounts of endpoint-related data in real time and detect potential threats. The earlier a hazard is identified, the sooner it can be contained, which is essential for minimizing losses.
Some tools are able to map anomalous behavior to the MITRE ATT&CK Framework, which expedites the identification of the type of attack observed.
Feeding Sources of Danger and Attack Vectors
Look for endpoint detection and response (EDR) systems that include information from major threat intelligence feeds to gain a better understanding of the threat behaviors and attack vectors that should be avoided. To improve your ability to identify the most recent forms of cyberattacks, you should ensure that the information from the threat feed is collected as frequently as possible, if not in real time.
The greater the number of threat feeds that an EDR tool subscribes to, the better; doing so reduces the likelihood that the program may overlook a newly discovered attack vector. Accepting feeds from many sorts of threat feed providers (such as cybersecurity providers, pure-play feed providers, cybersecurity organizations, and law enforcement bodies) can be beneficial in identifying a wide variety of attack vectors. This can be accomplished by accepting feeds from multiple types of threat feed providers.
Having the ability to react
The most effective endpoint detection and response (EDR) technologies not only recognize possible dangers and warn personnel about them, but they also take preventative measures automatically, such as preventing harmful behavior on compromised endpoints and taking other measures to reduce potential losses.
Look for solutions that have extensive live response capabilities, such as the ability to automatically drop into a compromised system and fix issues or run scripts and commands to help with triage. It is incredibly important to discover tools that give these capabilities, and you will not find them in all EDR solutions, so make sure to make it a priority in the selection process. Since it is extremely important to find tools that offer these capabilities, you will not find them in all EDR solutions.
If you are unable to locate an EDR tool that satisfies your requirements or price range and has live response capabilities, you should look for a solution that at the very least will identify remediation measures for you to do. This will allow you to respond to problems more quickly.
Top5 EDR Tools in the industry
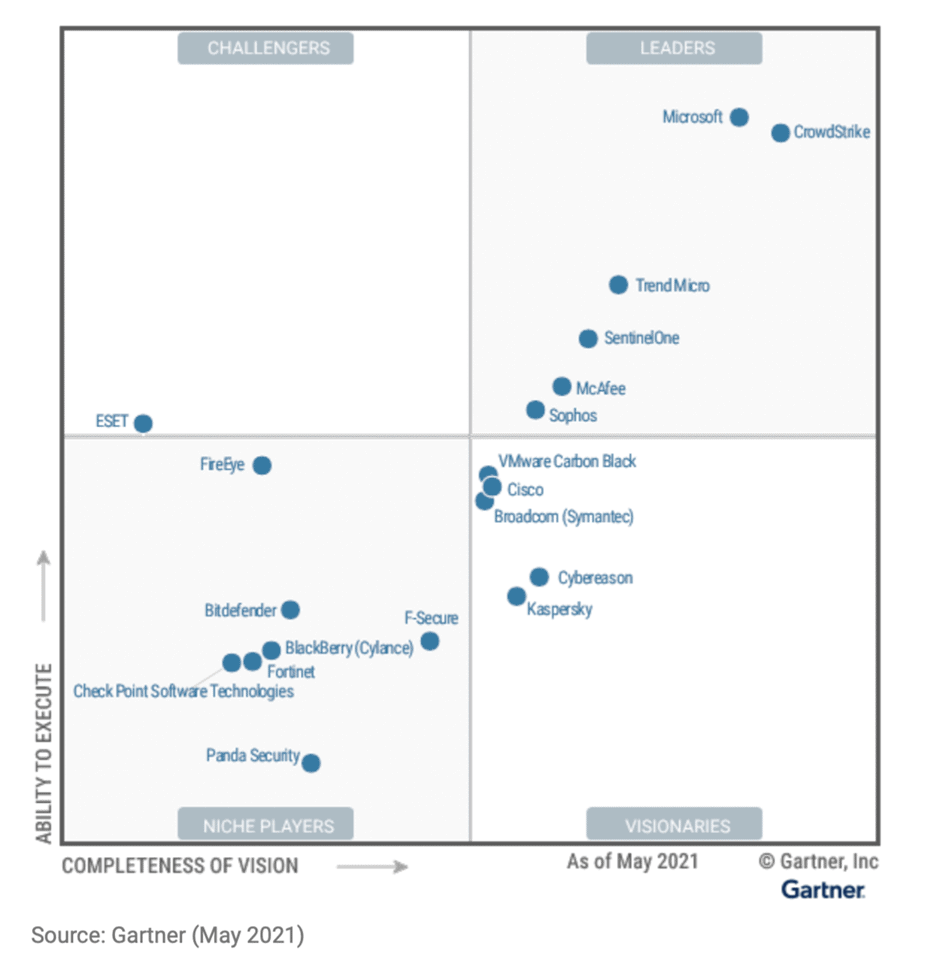
As per Gartner’s Magic Quadrant for EDR platforms, CrowdStrike Falcon, Microsoft Defender, TrendMicro XDR, SentinelOne’s Singularity XDR, McAfee’s Trellix EDR, and Sophos’s Intercept X are in the leaders quadrant in the same sequence. However, as per the number of ratings, Sentinel One’s Singularity XDR, CrowdStrike Falcon, VMware Carbon Black EDR, TrendMicro XDR, and Check Point’s Harmony Endpoint are in the top 5.
My personal choice is always CrowdStrike Falcon since 4th quarter of 2021, based on my recent deployment experience, product capability, service & supportability, and percentage of people who recommends Falcon which includes me too. My second choice is SentinelOne’s Singularity XDR and my 3rd choice could be Microsoft Defender and this might be vary based on their product developments.
Magic Quadrant for Endpoint Protection Platforms
As mentioned, CrowdStrike Falcon, Microsoft Defender, TrendMicro XDR, SentinelOne’s Singularity XDR, McAfee’s Trellix EDR, and Sophos’s Intercept X are in the leaders quadrant in the same sequence.
Do we have any buyer’s guide or checklist to evaluate ?
To determine which EDR product is best suited for your company, you need to have a comprehensive understanding of the following first and using my buyer’s guide checklist, you can figure out the right product of your choice and feel free to reach me incase of any queries
Before making an investment in an EDR product, every security team needs to address all the questions that are covered in this buyer’s guide checklist.
How can I Help?
I am here to assist you if you have any concerns regarding EDR tools, require training for your employees, or would want assistance selecting tools, testing them, or integrating them in your environment.
I have experience assisting some of the most successful firms in the world with the implementation of EDR technologies, and I would be honored to have the opportunity to advise you on the deployment of these critically important solutions. I have previous expertise with a wide variety of EDR solutions, including those that run on Windows, Unix, Linux, Mac OS, and a wide variety of other device-specific operating systems. I am a consultant, not a provider of tools; as a result, I can be entirely objective while assisting you in selecting the tools that will be most beneficial to your firm, irrespective of the provider of those tools.
Give me a call at (91) 9686908402 or send me an email at [email protected] if you are interested in learning more about the EDR tools that I can assist you with and how I can do so.















